The development of systems is a very demanding task. Their complexity has continued to grow due to the increasingly established applications in areas such as telemedicine, Industry 4.0, etc.
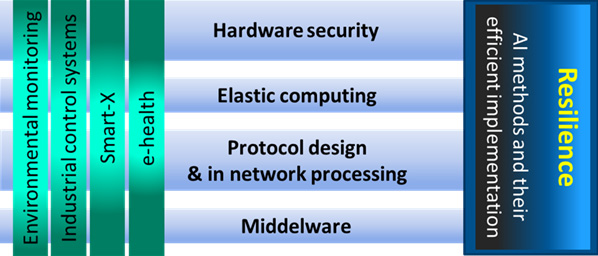
In these areas of application, an extremely high reliability of the systems is expected, since human lives are at risk in the event of malfunctions or functional failure. The wireless systems department uses a holistic approach to investigate the design and implementation of such complex Cyber Physical Systems of Systems (CPSoS) using selected, highly innovative applications. Figure 01 illustrates this approach. On the left the fields of application are shown that influence the work in the research areas shown horizontally. The aim is to show that all research issues are relevant for all areas of application. Resilience is all-important and quite rightly so. Resilience of the CPSoS is the ultimate goal of development. Therefore, all other research questions must be included here. This also applies in particular to the application of artificial intelligence methods which are constantly gaining importance in the horizontally presented approaches to new solutions, as well as an indispensable component of resilient systems. In addition to the investigation of individual solution approaches, the development of a design methodology that ensures the resilience of systems is a central topic, even if this is not shown in Figure 01 for reasons of complexity.
A weighted analysis results in the following allocation to the two groups:
Sensor networks and middleware platforms
-
Elastic computing >> click here <<
Elastic computing is a highly topical, highly innovative research area that is only just developing. In this research field, questions such as ensuring Quality of Service and Quality of Experience (QoE) in hybrid networks through intelligent bundling of transmission channels and load balancing between edge-fog-cloud can be achieved with the help of AI-supported measures. With load balancing, the aspects of confidentiality, integrity and protection of privacy will become significantly more important in the higher layers. For example, in the area of 5G campus networks patient data is transmitted and processed. If, at the same time, the processing location is dynamically adapted to the current network load, suitable “processing containers” must be developed that can guarantee the confidentiality of the data as well as the processing algorithms. The challenge here is that these containers can be used in potentially "hostile" environments. “Hostile” here means execution outside the jurisdiction of the owner of the data or algorithms and on possibly unknown hardware. The first project proposals for elastic computing are in preparation.
-
Protocol design & in-network processing >> click here <<
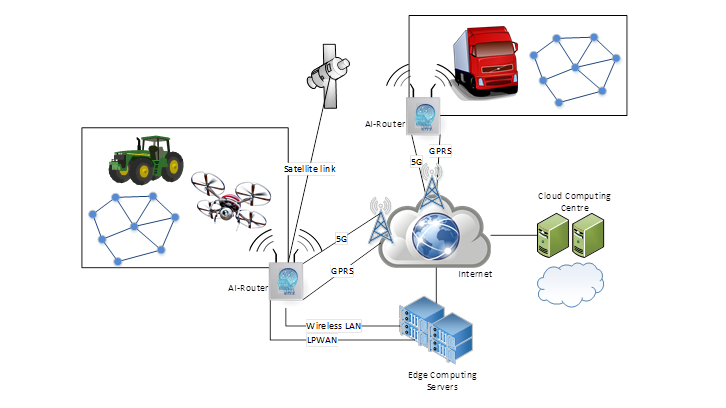
The use of wireless and mobile sensor networks, e.g. in the application areas Agriculture 4.0 or Industry 4.0, requires the development of new protocols that in particular take these changed operating conditions into account. This includes mobility-related changes in the reliability and availability of network connections, real-time requirements in the field of autonomous systems, etc. Therefore, it should be examined whether and under which conditions network protocols can be independently adapted by the networks to change the quality of service or quality of experience parameters and how the consistency of the protocols in larger networks can be guaranteed. The applications must also be taken into account here. The latter essentially relates to the question of processing the sensor data. In the DAKIS KI project, for example, processes and their implementation on FPGAs are investigated in order to be able to determine animal noises near the microphones with which they are recorded. This clearly shows cross-references to the topic of elastic computing.
-
Middleware >> click here <<
Middleware serves to simplify application development by realizing a uniform interface to heterogeneous distributed systems. This allows the developers to concentrate on their main task, the application, and details such as data exchange or data security are implemented in the middleware layer. The focus of the investigations is on the integration, in particular, of resource-limited systems such as wireless sensor networks with cloud systems. This has an impact on the protocols and programming models used. The aspects of security and privacy are the core research topics. The challenge arises from the different capacities of the interacting systems, which still have to be able to guarantee the same level of security and privacy. The use of a universal middleware in several areas of application (SmartGrid, SmartCity, environmental monitoring, etc.) also allows better recording of the situation through data fusion. The core of the middleware was implemented in the e-balance and SmartGrid platform projects and is being further developed in the SmartRiver and e-balance-plus projects.
Total resilience
-
Hardware Security >> click here <<
The holistic view of IT security aspects is of particular importance for the working group Total Resilient Systems and is of great social importance due to the growing security problems. The main aim of this work is to provide secure implementations, in the sense of being protected against various attacks such as side channel and error injection attacks. In the last few years, implementations of cryptographic operations have predominantly been considered. Here, methods of artificial intelligence were and are used both to carry out attacks and to detect attacks. In the Morfeus and KISS projects in particular, methods for detecting attacks are being investigated. In the future, the investigation of attacks against methods of artificial intelligence will be driven forward, since such attacks, if they are successful, among other things, can violate the privacy of users and also endanger system properties such as resilience. Since the AI methods are to be used in embedded systems, the investigations essentially focus on hardware implementations of the AI methods.
-
Artificial intelligence methods >> click here <<
The focus of the investigations is the applicability of artificial intelligence methods in embedded, i.e. resource-limited, systems. This creates two extraordinary challenges. First, embedded systems only have limited computing power, so that complex AI methods cannot be used, at least in the software. As already started in the Morfeus project, hardware accelerators are being developed to meet this challenge. Another extremely exciting approach is the investigation of hybrid solutions in which complex AI methods e.g. analyze large amounts of data in the cloud and use the results obtained in this way to evaluate the data in real time with the help of simpler methods of signal processing in embedded systems. This approach was first considered in the fast-gait project. The second challenge arises from embedded systems. Only a very limited amount of data is available, so it is unclear whether it is even possible to train AI methods with these amounts of data. This problem is being investigated in the KISS project for network attacks against critical infrastructures.
-
Resilience: metrics, specific solutions and design methodologies >> click here <<
This topic will become more and more important in the future with the introduction of autonomous, intelligent systems. This is derived from the definition of resilience, which means that a technical system reacts intelligently to events that can and cannot be planned, whereby the functionality of the system can be kept in a safe area or returned to this area. This extremely challenging task can be achieved by developing integrative solutions together with the other research fields and the other research programs of the IHP. Determining the resilience of a system is still an unsolved task. For this purpose, generally accepted metrics must be developed and their ability to actually measure resilience must be demonstrated. The challenge here is how do you determine the ability of a system to correctly react to unknown situations? At best, this ability can be tested indirectly. Possibly, partial metrics must be used for better understood aspects and their combination must be examined and evaluated as the basis for a more complex metric. Another possibility would be to provide metrics with a kind of "fuzziness" relation that makes the conditional expressiveness of individual values comprehensible. In addition to the question of assessing resilience, approaches that serve to make systems more resilient are examined. There is a clear cross-reference to the topic of IT security on the one hand and to the topic of reliability, which is processed in the System Architectures department. The knowledge gained when designing such “partial solutions” should lead to a design methodology or at least guidelines that enable engineers to achieve “resilience by design”. For this purpose, the individual solutions are to be transferred to a modular system and thus made reusable.
One approach that is to be specifically examined here is the balancing act between the resistance of cryptographic circuits to side-channel and manipulation attacks which on one hand is an important problem that can be solved by using novel gates, e.g. the IHP radiation-hard JICG or TMR-based gate. On the other hand, an intelligent dynamic reconfiguration of redundant blocks (modules) was conceived as a complementary solution. Another starting point is the resistance of the IHP RRAMs to manipulation, e.g. by means of localized optical defect injections, which are examined in the Wireless Systems department in cooperation with Materials Research Department The manipulation resistance of the RRAM cells or the methods for increasing the resistance, play a significant role when using RRAM structures as hardware accelerators of the AI methods.
In addition to the aspects already mentioned, the transfer of resilience approaches from nature will be examined in the future. A particularly interesting example are octopuses whose arms can still at least partially perform tasks correctly which they have learned after the “brain” has been cut off.